Welcome to our comprehensive guide on mastering the art of deleting event logs! In the realm of cybersecurity and system maintenance, understanding how to delete event logs is a crucial skill. Whether you are troubleshooting issues, ensuring data privacy, or simply optimizing system performance, knowing the ins and outs of event log management is essential. Our step-by-step guide will walk you through the process, demystifying this often overlooked aspect of system administration.
By the end of this blog, you will be equipped with the knowledge and tools to confidently manage and delete event logs, safeguarding your system and enhancing its efficiency. Let’s delve into the intricacies of event log deletion and empower you to take control of your system’s logs.
Introduction to Event Logs
Event logs are records of occurrences that happen within an operating system, application, or a device. They provide valuable information about the system’s activities, errors, and security events. Understanding event logs is crucial for monitoring the health and security of a system.
Types of Event Logs
There are several types of event logs that serve different purposes. These include:
- System Logs
- Application Logs
- Security Logs
- Setup Logs
Importance of Event Logs
Event logs play a vital role in diagnosing issues, troubleshooting errors, and investigating security incidents. By analyzing event logs, administrators can identify patterns, anomalies, and potential threats to the system’s integrity.
Importance of Managing Event Logs
Event logs are vital records that provide critical insights into the operations and security of a system. Managing event logs is crucial for maintaining the integrity and security of the system. Effective management of event logs ensures that all activities, errors, and security incidents are properly recorded, monitored, and analyzed.
Enhances Security
Managing event logs helps in detecting and responding to security threats promptly. By monitoring logs regularly, suspicious activities can be identified early on, enabling the system administrators to take necessary actions to prevent security breaches.
Facilitates Troubleshooting
Well-maintained event logs provide valuable information for troubleshooting issues within the system. When errors occur, event logs can be used to track the sequence of events leading to the problem, making it easier to diagnose and resolve technical issues.
Regulatory Compliance
Managing event logs is essential for meeting regulatory compliance requirements. Many industries have strict regulations that mandate the collection and retention of log data for auditing and security purposes. Proper management of event logs ensures that organizations remain compliant with relevant regulations and standards.
Understanding the Risks of Keeping Event Logs
Event logs record crucial information about system activities, such as logins, access attempts, and errors. While keeping event logs can be beneficial for troubleshooting and security monitoring, there are significant risks associated with retaining them indefinitely.
Potential Risks:
Keeping event logs for extended periods can lead to:
- **Data Breaches:** Storing sensitive information in logs poses a security risk.
- **Compliance Violations:** Failure to adhere to data retention regulations can result in legal penalties.
- **Resource Drain:** Accumulating logs can strain storage capacity and impact system performance.
Best Practices for Managing Event Logs:
To mitigate these risks, consider implementing the following practices:
- Regularly review and purge old logs that are no longer needed.
- Implement encryption and access controls to protect log data.
- Automate log management processes to ensure timely maintenance.

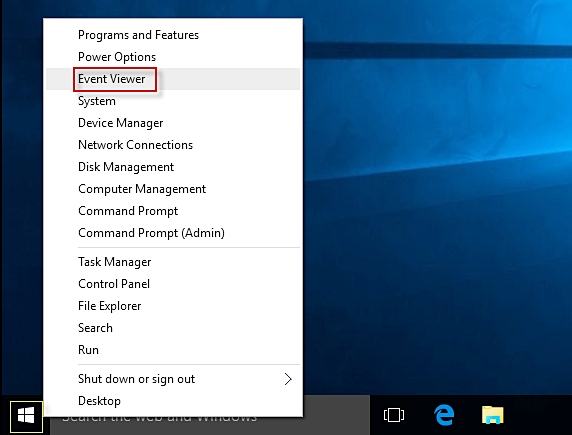
Step 1: Accessing Event Logs on Windows
Accessing event logs on Windows is essential for monitoring system activities and troubleshooting issues effectively. Follow these steps to access event logs on your Windows system:
Using Event Viewer
To access event logs, the primary tool in Windows is the Event Viewer. You can open Event Viewer by typing “Event Viewer” in the Windows search bar or by pressing Windows key + X and selecting “Event Viewer” from the menu.
Within Event Viewer, you can navigate through different categories of event logs such as Application, Security, Setup, System, etc., to view specific types of events and their details.
Filtering Event Logs
Once in Event Viewer, you can filter event logs based on various criteria such as date and time, event level, source, or keywords to narrow down the search results and find specific events quickly.
By applying filters, you can focus on relevant events that can help you in diagnosing and resolving issues effectively.

Step 2: Reviewing Event Logs for Relevant Data
Once you have accessed the event logs on your system, the next crucial step is to review them for any relevant data that may provide insights into system activities and potential issues. Event logs are a treasure trove of information that can help you understand what is happening on your system, identify security breaches, or troubleshoot technical issues.
Identifying Key Events
Start by scanning the event logs for critical events such as system errors, warnings, or security incidents. These events are typically marked with specific event IDs that can help you pinpoint the exact nature of the issue. Look for patterns or anomalies that could indicate potential problems.
Filtering by Time and Source
Use time-based filters to narrow down your search to a specific time frame when the event of interest occurred. You can also filter logs by event source to focus on logs generated by specific applications or services. This can help in isolating the relevant data and simplifying the analysis process.
Correlating Events
Often, a single event may not provide the full picture. It’s essential to correlate multiple events to understand the sequence of activities or incidents leading to a particular issue. Look for dependencies or relationships between different events to uncover the root cause effectively.
Step 3: Deciding What to Delete
When it comes to managing event logs efficiently, deciding what to delete is a crucial step. By prioritizing the logs based on relevance and importance, you can optimize your system’s performance and storage utilization.
Identification of Redundant Logs
Start by identifying redundant logs that no longer serve a purpose. These could include old system notifications, duplicate entries, or logs from processes that are no longer active. Deleting these logs can free up valuable space.
Retention Policy Analysis
Review your organization’s retention policies to determine the required duration for storing specific logs. By adhering to these guidelines, you can safely delete logs that have exceeded their retention period while ensuring compliance with data regulations. Ensuring compliance is essential for data security.
Unused Logs Cleanup
Unused logs, such as those related to discontinued applications or services, can be safely deleted to declutter your log repository. Create a checklist of these unused logs and systematically remove them to streamline your log management process.
- Identify logs from obsolete applications
- Verify the importance of logs for current operations
- Delete logs that are no longer relevant
Step 4: Deleting Event Logs Safely
When it comes to maintaining the security and performance of your system, deleting event logs is a crucial step. By safely removing these logs, you can free up space, prevent unauthorized access to sensitive information, and improve overall system efficiency.
Using Built-in Tools
To delete event logs safely, you can utilize the built-in tools provided by the operating system. For Windows users, the Event Viewer allows you to view and clear logs efficiently. Simply navigate to the Event Viewer, select the log you want to delete, right-click, and choose the “Clear Log” option. Remember to backup important logs before deleting them.
Automate Log Deletion
For a more streamlined approach, consider automating the deletion of event logs. You can use scripting languages like PowerShell or third-party tools to create scheduled tasks that routinely clear out old logs. This not only saves time but also ensures that logs are regularly purged, reducing the risk of data breaches.
- Start by creating a PowerShell script to delete specific event logs.
- Set up a scheduled task to run the script at designated intervals.
- Monitor the task to ensure logs are being deleted as intended.
Tips for Efficient Event Log Management
Managing event logs efficiently is crucial for maintaining system health and security. Here are some key tips to help you master the art of deleting event logs:
Regularly Review Event Logs
It’s important to regularly review event logs to identify potential issues before they escalate. Schedule routine checks to stay on top of system performance.
Set Up Automated Alerts
To stay proactive, configure automated alerts that notify you of critical events in real-time. This will help you address issues promptly and prevent system downtime.
Frequently Asked Questions
-
- Why is it important to delete event logs?
- Deleting event logs can help free up storage space, improve system performance, and enhance security by removing potentially sensitive information.
-
- What are the steps involved in deleting event logs?
- The steps usually involve accessing the event viewer, selecting the logs to delete, right-clicking to clear or delete them, and confirming the action.
-
- Can deleting event logs cause any issues?
- While deleting event logs is generally safe, it is important to be cautious as some logs may contain critical information for troubleshooting issues. Make sure to only delete logs that are no longer needed.
-
- How often should event logs be deleted?
- The frequency of deleting event logs may vary depending on the system usage and security requirements. It is recommended to establish a regular schedule for log maintenance.
-
- Are there any tools available to assist in deleting event logs?
- Yes, there are various software tools available that can automate the process of deleting event logs, making it easier and more efficient to manage logs across multiple systems.
Unlocking the Power of Deleting Event Logs
Mastering the art of deleting event logs is a crucial skill for optimizing system performance and ensuring data security. By following the step-by-step guide outlined in this blog, you can effectively manage and delete event logs to maintain a tidy and efficient system environment.
Remember, knowing how to delete event logs properly not only frees up valuable storage space but also helps in troubleshooting issues by providing a clean slate for monitoring and analysis.
In summary, deleting event logs is not just about clearing clutter – it’s about empowering yourself to control your system’s health and security. Take charge of your system maintenance today and reap the benefits of a well-managed log management strategy.