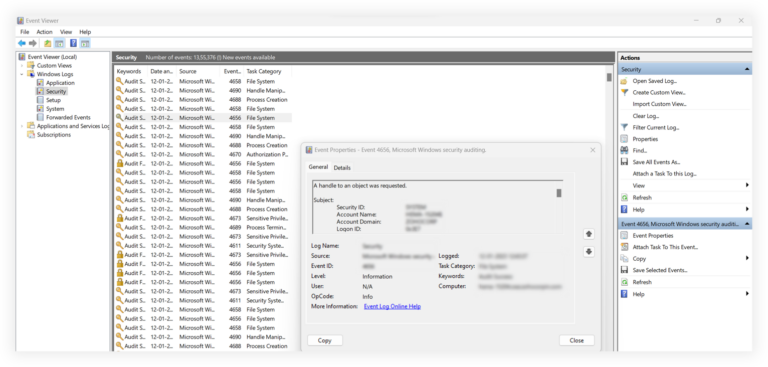
Have you ever wondered, “what is event log?” This essential tool holds a key to understanding the inner workings of your system. Event logs are like a digital diary, capturing important events and errors that occur within your computer system. From system updates to security breaches, the event log provides a trail of breadcrumbs for IT professionals to analyze and troubleshoot issues effectively. In this blog, we will delve into the mystery behind event logs, uncovering their significance and how they play a crucial role in maintaining system health and security. Join us as we demystify the world of event logs and unlock their potential for optimizing system performance.
Introduction to Event Log
An event log is a record of events that occur on a computer, network, or software application. It provides valuable information for system administrators, developers, and security professionals to troubleshoot issues, monitor performance, and analyze the health of the system.
Importance of Event Log
Event logs play a crucial role in identifying security breaches and understanding system behavior. They help in detecting unauthorized access attempts, auditing system activities, and diagnosing errors.
Types of Event Logs
There are various types of event logs, including system logs, security logs, application logs, and setup logs. Each type records specific events related to the corresponding part of the system.
Importance of Event Log
An event log is a crucial tool that records significant events happening on a computer system or network. It provides valuable insights into the activities, errors, and security-related incidents occurring within an IT environment. By monitoring and analyzing event logs, organizations can enhance their system’s performance, troubleshoot issues efficiently, and strengthen their overall security posture.
Enhances Security
The event log plays a critical role in enhancing security by recording login attempts, access control activities, and potential security breaches. Security teams can proactively identify and respond to threats by analyzing patterns and anomalies within the event logs.
Effective Troubleshooting
When technical issues arise, event logs serve as a diagnostic tool to pinpoint the root cause of problems. IT administrators can quickly resolve issues by examining the timestamps, error codes, and descriptions provided in the event logs.
Components of Event Log
An Event Log is a crucial tool that records significant events occurring on a computer system or network. Understanding its components is essential for effective system monitoring and troubleshooting.
Event ID
The Event ID is a unique identifier assigned to each event logged. It helps in categorizing and tracking specific occurrences within the log.
The Event ID provides valuable insight into the nature and source of an event, aiding in diagnosing issues.
Timestamp
The Timestamp indicates the date and time when an event was logged. It is crucial for understanding the sequence of events and establishing timelines.
Having an accurate Timestamp is vital for identifying the occurrence and duration of events, aiding in the resolution of technical issues.
Description
The Description provides detailed information about the event, including its nature, impact, and potential causes. It offers context for interpreting the logged events.
Understanding the Description helps in analyzing the events recorded in the log and taking appropriate actions to address any anomalies or errors.
Benefits of Event Log
Event logs are crucial tools that provide valuable insights into the workings of a system, network, or application by recording important events in real-time. These logs offer several benefits for businesses and IT professionals that can enhance security, troubleshooting capabilities, and overall system performance.
Enhanced Security
One of the primary benefits of event logs is the enhancement of system security. By tracking and monitoring all system activities, event logs enable administrators to detect and respond to security incidents promptly. This helps in identifying potential threats, unauthorized access attempts, and other security breaches effectively.
Improved Troubleshooting
Event logs play a vital role in troubleshooting system issues by providing detailed records of past events. When a problem arises, IT professionals can analyze event logs to pinpoint the root cause of the issue quickly. This leads to faster resolution times and prevents recurring problems.
Performance Monitoring
By monitoring system events and activities, event logs help in assessing the performance of applications and systems. By analyzing event logs, businesses can identify performance bottlenecks, track resource usage trends, and optimize system configurations for efficient operation.
How to Interpret Event Log Data
Understanding how to interpret event log data is crucial for maintaining the security and functionality of your systems. Event logs provide valuable information about the activities and health of your system. Here are some key steps to help you make sense of event log data:
1. Start by Reviewing Event Types
Event logs categorize events into different types such as Information, Warning, and Error. Information events are typically routine operational messages, while Warning and Error events indicate potential issues that need attention (2022 data).
2. Identify Patterns and Anomalies
Look for patterns or abnormalities in event log data that may indicate security breaches, system failures, or performance issues. Pay attention to recurring events or sudden spikes in activity to catch potential issues early.
3. Utilize Event Log Analysis Tools
Use specialized event log analysis tools or software to help you efficiently parse through large volumes of event log data. These tools can provide insights, alerts, and visualizations to streamline the analysis process.
Image: Visualizing event log data for system analysis
Frequently Asked Questions
-
- What is an Event Log?
- An Event Log is a record of events that happen on a computer, device, or software application. It provides valuable insights into the system’s activities and can help with troubleshooting issues.
-
- Why is the Event Log an essential tool?
- The Event Log is essential because it helps in monitoring the system’s health, identifying potential problems, tracking security events, and diagnosing issues when they occur. It is a valuable resource for system administrators and IT professionals.
-
- How can I access the Event Log on my computer?
- You can access the Event Log on Windows computers by going to the Event Viewer tool in the Control Panel or using the Event Viewer application. On Linux systems, you can access the Event Log through the syslog or journald service.
-
- What kind of information is typically found in an Event Log?
- An Event Log contains information about system errors, warnings, informational messages, security events, application crashes, and more. It logs events related to hardware and software changes, user activities, and system processes.
-
- Can I customize the Event Log to track specific events?
- Yes, you can customize the Event Log on most systems to track specific events or create custom event logs. This allows you to focus on monitoring the events that are relevant to your system’s operation or security.
Unlocking the Power of Event Logs: A Vital Insight
As we unravel the essence of event logs, it becomes evident that this indispensable tool holds the key to monitoring system activities, troubleshooting issues, and enhancing cybersecurity. Understanding what event logs are and how they function grants us the ability to proactively manage our systems, identify potential threats, and optimize performance. By delving into the intricacies of event logs, we equip ourselves with a powerful resource that empowers us to safeguard our digital environment effectively. Embracing the significance of event logs paves the way for enhanced security measures, streamlined operations, and resilient network infrastructures. In essence, the mystery behind event logs is no longer elusive but a valuable asset in our technological arsenal.