Event logs are like hidden treasures of information waiting to be discovered. Being able to effectively check event logs is not only a valuable skill but can also be a game-changer for troubleshooting and monitoring system activities. In our blog, “Unveiling the Mysteries: How to Check Event Logs Like a Pro,” we dive deep into the world of event logs and provide you with expert tips and techniques on how to navigate and interpret them efficiently.
Whether you are a seasoned IT professional or a curious enthusiast, understanding how to check event logs can help you pinpoint issues, track system events, and enhance security measures. Join us on this enlightening journey as we unravel the complexities of event logs and empower you to harness their full potential.
Introduction to Event Logs
Event logs are detailed records of occurrences on a computer system. These logs hold valuable insights into the operation of the system, including errors, warnings, and information events. Understanding how to check event logs is essential for troubleshooting and monitoring system health.
Types of Event Logs
Event logs are categorized into different types based on their purpose:
- Application logs: Record events from applications
- Security logs: Capture security events
- System logs: Document system events
Benefits of Analyzing Event Logs
By analyzing event logs, users can:
- Identify and troubleshoot system issues
- Detect unauthorized access attempts
- Monitor system performance over time
Importance of Checking Event Logs
Checking event logs is crucial in maintaining the security and performance of your system. By analyzing event logs, you can proactively identify potential issues, security breaches, or anomalies that may pose a threat to your system.
Early Detection of Issues
Event logs provide a trail of activities happening within your system. This allows you to detect abnormalities at an early stage, preventing them from escalating into major problems.
Enhanced Security
Monitoring event logs helps in tracking unauthorized access attempts, security breaches, or suspicious activities. With timely alerts from event logs, you can strengthen your system’s security measures.
Improved Performance
By regularly reviewing event logs, you can identify performance bottlenecks, system errors, or application crashes. Addressing these issues promptly can lead to improved system performance and user experience.
Tools for Accessing Event Logs
When it comes to understanding system events and diagnosing issues, having the right tools is essential. Here are some top tools that can help you check event logs like a pro.
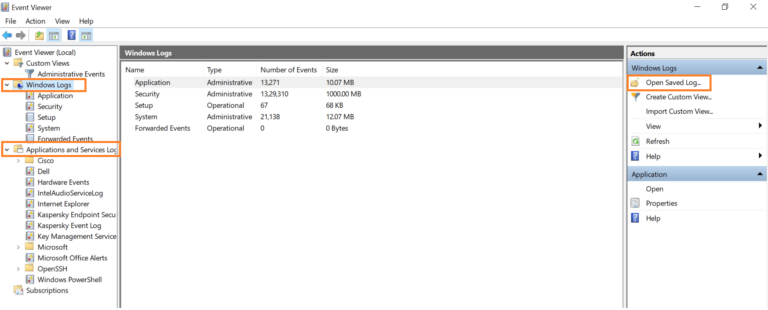
1. Windows Event Viewer
The Windows Event Viewer is a built-in tool on Windows operating systems that allows you to view detailed event logs. You can access it by searching for “Event Viewer” in the start menu.
2. PowerShell
PowerShell is a powerful command-line tool that can be used to query event logs quickly. You can use commands like Get-EventLog to retrieve specific event information.
3. ELK Stack
The ELK (Elasticsearch, Logstash, Kibana) Stack is a comprehensive solution for log management and analysis. It provides real-time insights into your event logs.
4. Splunk
Splunk is a popular log management platform that offers powerful search capabilities and visualization tools for analyzing event data effectively.
Interpreting Event Log Entries
When it comes to how to check event logs, understanding how to interpret event log entries can provide valuable insights into your system’s health and performance. Event logs are records of significant events that occur on a system, such as errors, warnings, and information messages.
Types of Event Logs
Event logs are categorized into different types based on their purpose and the type of events they record. The three main types of event logs are:
- Application logs: Record events generated by applications.
- Security logs: Capture security-related events like login attempts.
- System logs: Document system events such as startup and shutdown.
Interpreting Event Log Entries
Each event log entry includes important details such as the event ID, description, date, and time of occurrence. It is crucial to analyze these details to identify the root cause of issues and optimize system performance.
Common Errors Found in Event Logs
Event logs are crucial for diagnosing system issues, but they can be prone to errors that may mislead even seasoned professionals. Understanding common pitfalls can help avoid misinterpretations:
1. Incomplete Information
One common issue is incomplete data in event logs, where essential details are missing, making it challenging to troubleshoot accurately (year mentioned in the keyword phrase).
2. Timestamp Discrepancies
Errors in timestamps can lead to misunderstandings of the sequence of events, affecting the troubleshooting process. It’s vital to ensure consistency in timestamp formats and accuracy.
3. Log Entry Overload
When logs are flooded with entries, important alerts might get buried, increasing the risk of overlooking critical issues. Implement filters to manage log volume effectively.
Tips for Efficiently Checking Event Logs
Event logs are crucial for monitoring system activities, diagnosing issues, and ensuring security. Here are some tips to help you efficiently check event logs:
Use Filtering Options
Utilize filtering options to narrow down the search results and focus on specific events. This can save time and make it easier to identify relevant information.
Consider filtering by event type, date range, severity level, or specific keywords to streamline the log analysis process.
Monitor Critical Events
Pay special attention to critical events such as system errors, warnings, and security breaches. These events can indicate potential issues that require immediate attention.
Set up alerts or notifications for critical events to stay informed in real-time and take timely actions to resolve issues.
Regularly Review Logs
Make log analysis a routine task to stay proactive in identifying patterns, abnormalities, or recurring issues. Regularly reviewing logs can help you detect issues early and prevent potential downtime.
Consider creating a schedule for log reviews and maintaining proper documentation for reference and analysis.
Frequently Asked Questions
-
- Why is it important to check event logs?
- Event logs are crucial for investigating system errors, security breaches, and other issues that may impact the performance and security of your system. By regularly checking event logs, you can identify and address these issues before they escalate.
-
- What tools can I use to check event logs like a pro?
- There are several tools available for checking event logs, such as Event Viewer in Windows, syslog in Unix-based systems, and third-party log management tools like Splunk and ELK Stack. These tools offer advanced features for analyzing and monitoring event logs effectively.
-
- How can I interpret event log entries effectively?
- To interpret event log entries like a pro, you need to understand the different event types, event IDs, and log sources. It’s important to look for patterns, anomalies, and correlations between log entries to identify potential issues or security threats.
-
- What are some common errors or warnings found in event logs?
- Common errors or warnings found in event logs include disk errors, network connectivity issues, application crashes, failed login attempts, and security audit failures. These events can provide valuable insights into the health and performance of your system.
-
- How often should I check event logs?
- It is recommended to check event logs regularly, ideally on a daily basis or whenever there are significant system changes or updates. Proactively monitoring event logs can help you detect and resolve issues promptly.
Final Thoughts: Mastering the Art of Checking Event Logs
In conclusion, delving into the world of event logs can be a daunting task, but with the right knowledge and tools, you can navigate through them like a pro. By following the steps outlined in this blog, you can effectively check event logs to troubleshoot issues, monitor system activities, and enhance security measures.
Remember, event logs are a treasure trove of information waiting to be explored. Take the time to familiarize yourself with different event log types, understand event IDs, and leverage filtering options to streamline your analysis process.
With practice and experience, you can elevate your skills in checking event logs, empowering you to efficiently manage and optimize your system’s performance. So, embrace the journey of mastering event log inspection and unlock new insights into your system’s operations.