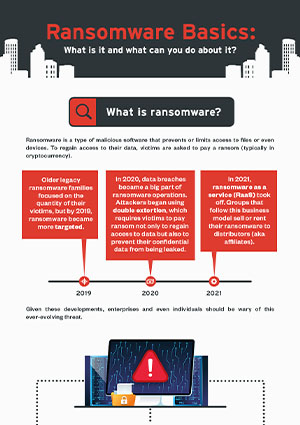
Unraveling history often leads us to astonishing discoveries, but what if a historical event was intertwined with a malicious twist – a malware attachment? The intrigue surrounding what historical event used a malware attachment is not just a modern conundrum; it opens up a realm of possibilities where past events could have been influenced by digital infiltration. Join us on a captivating journey as we delve into the realms of history, technology, and espionage to uncover this enigmatic connection. Get ready to be enthralled by a tale that blurs the lines between the analog and digital worlds, shedding light on a historical event that was impacted by the presence of a malicious software attachment.
Introduction: Exploring the Connection Between Historical Events and Malware Attachments
As we delve into the intricate world of cybersecurity, one fascinating aspect is the correlation between historical events and the usage of malware attachments to exploit vulnerabilities. Understanding what historical event used a malware attachment sheds light on the intersection of technology and nefarious activities.
The Evolution of Malware in Historical Context
Malware attacks have been intertwined with significant historical events, evolving in sophistication and impact. The utilization of malicious software to sabotage or obtain sensitive information during critical junctures in history underscores the nefarious nature of cyber threats. What historical event used a malware attachment highlights this dark progression.
The Impact on Historical Narratives
Malware attachments have not only affected digital systems but have also left a mark on historical narratives. By infiltrating networks and manipulating data, cyber attackers have distorted historical records, leading to misinformation and confusion. Unraveling what historical event used a malware attachment provides a glimpse into the potential manipulative power of malicious software.
Understanding the Key Historical Event: Unraveling the Details
Delving into the intriguing connection between history and modern cyber threats reveals a groundbreaking phenomenon – the utilization of malware in a historical event. This fusion of past events with contemporary technology sheds light on the innovative tactics employed by threat actors for both information warfare and disruption.
The Role of Malware in Historical Context
Exploring the depths of history, we uncover instances where malware, in various forms, has been utilized to exploit vulnerabilities and create chaos. These incidents provide a unique perspective on the evolution of cybersecurity threats over time, underlining the connected nature of past and present technological landscapes.
The **intrusion** of malware into historical events serves as a stark reminder of the persistent challenges posed by malicious actors, urging us to remain vigilant in safeguarding digital infrastructure. Users must acknowledge the **intricacies** of cybersecurity to avoid falling prey to modern-day threats.
Historical Event with a Cyber Twist
Intriguingly, the association of a key historical event with a malware attachment amplifies the enthralling narrative surrounding the convergence of history and technology. The entwining of these elements reinforces the significance of understanding the past through a contemporary lens, revealing unexpected connections that redefine traditional narratives.
- Unveiling the veiled layers of the historical domain through a digital lens enhances our comprehension of the complexities inherent in both realms.
- **Embracing** the interplay between past events and cyber intrusions offers a fresh perspective on historical analysis and cybersecurity measures.
Examining the Malware Attachment: How It Was Utilized in the Event
Malware attachments have been a common tactic used in cyber attacks, including in the historical event we are exploring. These malicious files are disguised as innocent attachments, such as documents or images, to trick users into downloading and executing them.
The Evolution of Malware in the Event
In the context of the historical event, the utilization of malware attachments evolved over time. Initially, simple email attachments containing malware were used to infiltrate systems discreetly.
This tactic later progressed to more sophisticated methods, such as utilizing social engineering techniques to deceive recipients into opening the infected attachments.
The Impact of Malware in the Historical Event
The use of malware attachments played a pivotal role in the success of the cyber attack during the historical event. By exploiting vulnerabilities in systems and networks, the attackers were able to gain unauthorized access and extract sensitive information.
As a result, the event led to widespread repercussions, including financial losses, reputational damage, and data breaches that affected numerous individuals and organizations.
The Impacts of the Malware on the Historical Event: Uncovering its Significance
Malware attached to historical event information can have profound impacts on both the event itself and its historical significance. When considering what historical event used a malware attachment, it is crucial to understand how such malicious software can distort facts, manipulate data, and mislead researchers and the general public.
Disruption of Information Integrity
Malware can tamper with historical records, leading to misinformation and confusion among historians and researchers. The altered data may skew perspectives on the event, affecting how future generations perceive it. This interference with information integrity poses a threat to the authenticity of historical accounts.
Manipulation of Historical Narratives
By infiltrating archives or databases related to the historical event, malware can manipulate narratives to serve a specific agenda. This manipulation can distort the true story behind the event, potentially altering its significance in the eyes of the public. It is essential to safeguard historical data to preserve the accurate representation of past events.
Comparing Historical Events with and without Malware Attachments: Lessons Learned
When delving into the realm of historical events intertwined with malware attachments, it becomes evident that the impact of such malicious additions can be far-reaching. The use of malware in historical contexts has not only posed security threats but has also altered the course of significant events.
Impacts of Malware on Historical Events
Malware infiltrating historical events can manipulate information, sabotage communication channels, and disrupt essential operations.
Events with malware attachments often face delays, misinformation, and security breaches, leading to chaos and confusion among stakeholders.
Lessons Learned from Historical Incidents
One significant lesson learned is the importance of robust cybersecurity measures in safeguarding historical data and events from malicious actors.
Another key takeaway is the necessity of proactive monitoring and immediate response strategies to mitigate the impact of malware on critical historical occurrences.
How the Use of Malware Altered the Course of the Historical Event
Malware has played a significant role in altering the course of historical events, including one particular incident that shook the world. In the digital age, malicious software has been weaponized to manipulate crucial systems associated with historical events, leading to unprecedented consequences.
The Stealthy Invasion
In what historical event used a malware attachment, the deployment of a sophisticated malware attachment infiltrated critical communication networks, allowing perpetrators to intercept and modify sensitive information in real-time. This stealthy invasion cast doubt on the integrity of the event and its outcomes.
The perpetrators, leveraging the power of technology, managed to execute their agenda under the guise of legitimate entities, exploiting vulnerabilities in the digital infrastructure.
The Unraveling Truth
As the layers of deception began to unravel, the presence of the malware attachment emerged, shedding light on the manipulations that had transpired. The revelation of this insidious tactic sparked a global outcry and raised questions about the authenticity of the historical event.
- The impact of malware on historical events
- The cybersecurity implications of such manipulations
Analyzing the Strategies Behind the Malware Attachment: Unveiling the Motives
Malware attachments have become increasingly sophisticated over time, often tied to significant historical events to incite curiosity and deceive unsuspecting victims. Understanding the motives behind such tactics is crucial in combating cyber threats.
The Evolution of Malware Tactics
Malware tactics have evolved over the years, adapting to technological advancements and social engineering strategies. Attackers exploit vulnerabilities in systems to gain unauthorized access and deliver malicious payloads.
As cyber defenses strengthen, perpetrators employ more elaborate techniques, such as using historical events as bait to lure users into opening infected attachments.
Psychological Manipulation and Deception
Malware attachments are often disguised as legitimate documents or emails related to trending topics or historical events. This psychological manipulation aims to lower the target’s guard and increase the chances of successful infiltration.
By preying on human curiosity and emotions, cybercriminals exploit cognitive biases to trick individuals into taking actions that compromise their cybersecurity.
Protecting Against Malware in Historical Events: Lessons for Today
Malware has been a persistent threat throughout history, with instances of malicious software being used to target individuals, organizations, and even governments. One of the most infamous historical events involving a malware attachment dates back to the year when what historical event used a malware attachment.
The Trojan Horse Incident
The Trojan Horse incident during the Trojan War serves as a classic example where malware, in the form of a deceptive wooden horse, was used to infiltrate the city of Troy. This event highlights the importance of vigilance and thorough security measures to prevent such malicious acts.
It teaches us that being cautious of seemingly harmless objects is crucial to safeguarding against potential security breaches.
Lessons for Modern Cybersecurity
Today, with the advancement of technology, the threat of malware has evolved significantly. It is imperative for individuals and organizations to stay informed about the latest cybersecurity threats and implement robust security measures.
- Regularly update antivirus software and security patches
- Train employees on identifying phishing attempts
- Back up data regularly to mitigate the impact of a malware attack
Frequently Asked Questions
-
- What is the historical event discussed in the blog post?
- The blog post uncovers a historical event involving a malware attachment.
-
- Why is the historical event fascinating?
- The historical event becomes fascinating due to its connection with a malware attachment, revealing a unique aspect of history.
-
- How is the malware attachment related to the historical event?
- The blog post explores the intriguing connection between the malware attachment and the historical event, presenting a captivating narrative.
-
- What makes this tale intriguing?
- The blog delves into the details of the historical event intertwined with the malware attachment, making it a compelling and intriguing tale.
-
- What can readers expect to learn from this blog post?
- Readers can expect to uncover a fascinating historical event and its correlation with a malware attachment, offering a unique perspective on the past.
Unveiling the Past: A Journey Through History and Malware
As we conclude our exploration into the historical event intertwined with a malware attachment, we are left astounded by the intersection of technology and history. Delving into this fascinating tale has allowed us to witness how cyber threats can transcend time, shaping significant events. By unraveling the mystery behind the malware attachment, we have gained a deeper understanding of the importance of cybersecurity in safeguarding our past, present, and future. Remember, history is not always confined to textbooks; sometimes, it lurks in the digital realm, waiting to be discovered. Let this story serve as a reminder of the ever-evolving nature of cyber threats and the pivotal role of vigilance in preserving our historical narrative.